There’s a tweet that has Twitter aflutter. It includes the news that Twitter inadvertently sent users’ email addresses a...
How Does the 2019 Cybersecurity Checklist Apply to Wilmington, NC?When considering how the 2019 cybersecurity checklist ...
It’s the Little Things When we think about cybersecurity, we might first imagine big data centers being guarded. Hacker...
I’d Like a Word with You In fact, I’d like a word with all 218 million of you. Yes, that is the number of users in the ...
October 1, 2019 — Breach Secure Now! today announced its commitment to National Cybersecurity Awareness Month (NCSAM), h...
Knowledge is power. And when it comes to fighting hackers, we need all the power we can collectively find. Educating y...
Instant Money…Maybe? The popular commercial asks, “What’s in your wallet?” and if you ask most anyone, it probably isn’t...
Are You a Hacker Helper? Here you go, let me get the door for you. Are you looking for access to my company’s network? ...
Security Risk Rate vs. Spend Rate According to the 2019 SMB IT Security Report from Untangle, 80% of the small to medium...
A New Approach to an Old Problem Resistance to yet another government regulation, a lack of understanding the complexiti...
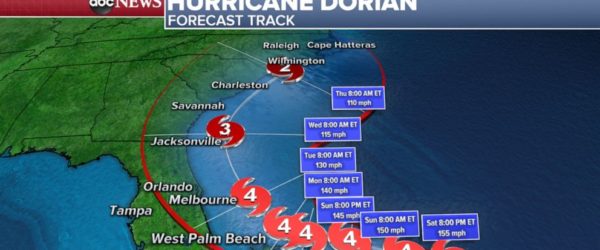
Hurricane Dorian is fast approaching and now is categorized as a 5. Your current backup and disaster recovery plans shou...
HIPAA – Then & Now The Health Insurance Portability and Accountability Act, better known as HIPAA, has been around s...