The Excuses It’s not easy! It’s a lot to keep track of. I have no idea where I’ve used that before. There’s nothing in ...
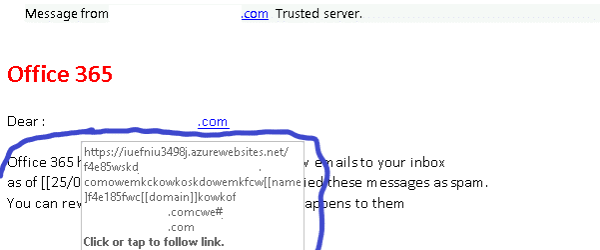
1. Who is it from? The number one easiest way to tell if an email you are reading is a phishing attempt is to read who t...
Watch Vlog #4 Below https://www.ipmcomputers.com/wp-content/uploads/2013/11/VLOG3.mp4
As regular users of computers, we like to be able to move through them as easily as possible. Some of us like to move fa...
Some Thoughts on Scam Sites & Scammers https://www.ipmcomputers.com/wp-content/uploads/2013/11/VLOG3.mp4
Thoughts on Custom PCs vs. Cookie Cutter PCs https://www.ipmcomputers.com/wp-content/uploads/2013/11/VLOG2.mp4
Some Thoughts on Email & Ransomware https://www.ipmcomputers.com/wp-content/uploads/2019/06/FB_20190612_154852.mp4
Most anti-viruses these days don’t prevent you from adding extensions to your web browsers. That is generally left...
Of the many things we do to protect our users, this is one of them. This is a script we implement across all our Exchang...
We are working on a 150 acre property out of South Carolina to provide a fiber back bone, as well as wireless network, a...
We are working on a newly built dental office utilizing 61 category6 network drops, 2 switches, 4 patch panels, 1 server...
Computer and network security: Everyone knows they should be doing it better, but no one really knows all the best ways ...